Key Takeaways
- Cybersecurity risks are on the rise as organisations adopt digital tools.
- From securing data to devices and training people, cybersecurity has many facets.
- Companies with a broad focus across multiple areas of cybersecurity potentially stand a better chance of enduring in a rapidly evolving industry.
- Related ProductsWisdomTree Cybersecurity UCITS ETF – USD AccFind out more
On 19 February, the Financial Times reported1 that North Korean cyber criminals were turning to artificial intelligence (AI) to steal funds and cutting-edge technologies from victims around the world. The report stated how hackers targeted global defence, cyber security, and crypto companies by tricking people on popular platforms like LinkedIn. It also stated that ChatGPT developer OpenAI and its investor Microsoft had also confirmed that bad actors were using their AI services for malicious cyber activities.
Generative AI tools have lowered the bar for people to do more technically sophisticated things with relatively basic skills. Large language models allow users to communicate with the computer in a language like English and let the model translate their commands to write programmes. Unfortunately, technology can also empower bad actors to do unlawful things more easily. This is why cybersecurity must become smarter and seal all potential vulnerabilities before criminals exploit them.
WisdomTree has partnered with venture group Team8 to identify eight distinct cybersecurity areas that are essential in a world with ever-increasing risks.
How investors can access the opportunity
WisdomTree Cybersecurity UCITS ETF has been built in partnership with cybersecurity industry experts Team8 and invests across eight different cybersecurity themes. The ETF provides investors with a pure exposure to the theme by only including companies that derive at least 50% of their revenue from cybersecurity activities. The ETF assigns an overweight to companies with fast revenue growth and a broad focus covering three or more of the eight themes. Companies with a broad focus across multiple areas of cybersecurity are deemed to stand a better chance of enduring if users look to consolidate the number of tools they use to protect their enterprises.
For cybersecurity to be thorough it needs to be holistic
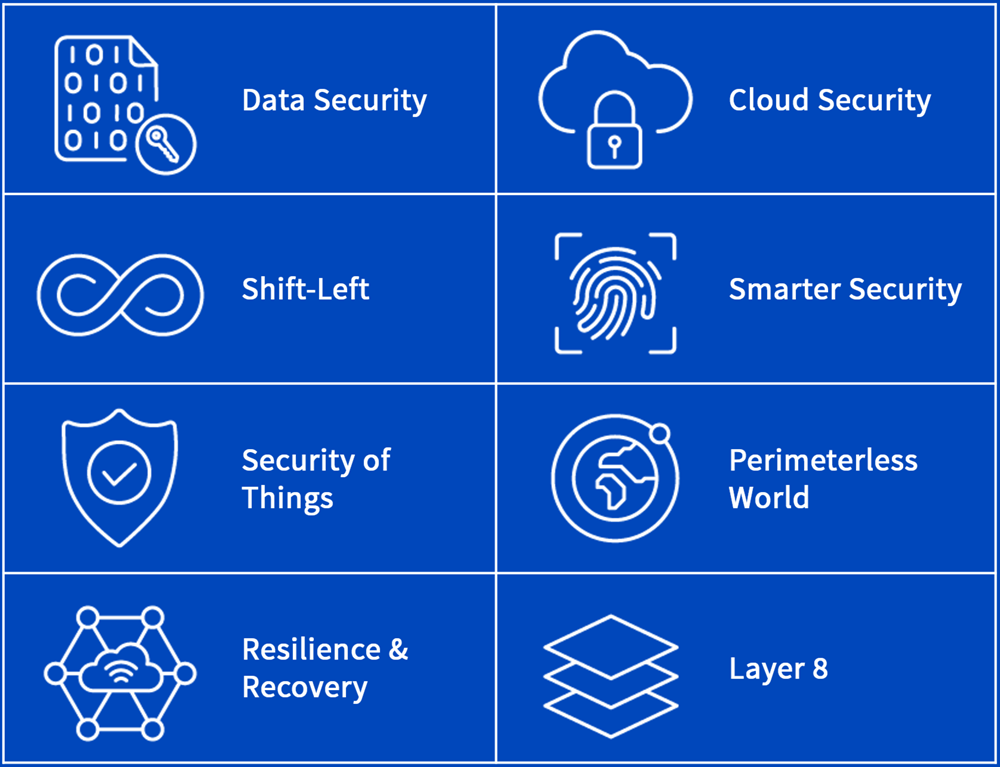
Data Security
It is estimated that the world produces 328 million terabytes of data every single day. One terabyte is 1000 gigabytes. In other words, the world is producing a lot of data. Moreover, the world is producing data faster than ever. It is also estimated that 90% of the world’s data was generated in the last two years alone2.
IBM states that the average data breach cost in 2023 was USD4.45 million, a 15% increase over three years3. With the world producing more data than ever, protecting that data is paramount. This is what data security aims to achieve.
Cloud Security
All this data being produced means more storage in the cloud. According to one report4, approximately 60% of all corporate data is stored in the cloud, up from just 30% in 2015. Moreover, 89% of companies use a multi-cloud approach, a term referring to a company using at least two cloud-based applications.
And unfortunately, malicious actors are fully aware of this. In 2023, there was a 110% increase in cloud-conscious cases5. This means that cyber adversaries are increasingly looking to attack their targets via cloud-based applications. Securing the cloud is, therefore, a critical theme in cybersecurity.
Shift-Left
Securing the cloud or any other application cannot be an afterthought. Shifting left refers to the idea of integrating cybersecurity at the point when the software is being developed. The opposite of this would be to keep cybersecurity right and rely on generic solutions from third-party providers.
Shifting cybersecurity left allows developers to critically evaluate vulnerabilities within the software to ensure all necessary guardrails are in place when the software is being created. This can reduce costs and expedite delivery as there will likely be fewer problems once the software has been introduced to users.
Smarter security
Generative AI has lowered the bar for becoming a bad actor. It is now easier to create malicious code, like that used in a polymorphic attack in which the cyber-attack changes code, content, and structure to avoid being detected by security systems. Such a code comes back stronger if it gets locked out by a company’s security.
Tackling such threats requires automation. Smarter security includes automation tools that can monitor networks for potential threats. This is where AI tools that learn, adapt, and evolve play a crucial role in providing security.
Security of things
The Internet of Things (IoT) refers to devices that are connected to the internet. Laptops and mobile phones are obvious examples but now, increasingly, cars, watches, digital assistants, TVs, dishwashers, and so forth, all belong to the IoT world. It is estimated that there are currently 17 billion IoT devices in the world, and this number could double by 20306.
Clearly, our devices need to be protected as they all provide attackers with points of entry for gaining access to our networks and data. The security of things, therefore, is the idea of protecting this growing number of connected devices from potential threats.
Perimeterless world
The so-called attack surface has grown, with organisations having a more significant number of remote workers since the COVID-19 pandemic. This attack surface refers to the sum of vulnerabilities that hackers can exploit to access an organisation’s network or sensitive data. Compared to the past, where workers may have been confined within a perimeter, attackers now have more potential entry points.
In a perimeterless world, organisations need more sophisticated tools for protecting themselves. This includes two-factor authentication and biometrics for users to log in to their company network and applications.
Resilience & recovery
In May 2017, the WannaCry ransomware attack cost the UK’s National Health Service £92m through services lost and IT costs. Even more importantly, 19,000 appointments were cancelled as more than 80 hospital trusts and 8% of GP practices were disrupted7.
According to Team8, cybersecurity cannot afford to stop at ‘identify, protect, detect, and respond’ but must also include the capability for rapid recovery from degradation, disruption, or denial of access to an organisation’s network or data. The cost of not being able to do so can be catastrophic.
Layer 8
An organisation may have the most powerful cybersecurity tools to protect itself. But, if the humans aren’t trained and equipped to handle risks, the guardrails may disintegrate like a house of cards. Layer 8, therefore, is the human factor.
According to CrowdStrike, 75% of attacks in 2023 were malware-free, up from 40% in 2019. This means that attackers are relying less on malware attacks delivered via phishing emails and using more sophisticated methods like social engineering, which are intended to deceive humans. Thus, empowering people to better manage cybersecurity risks can be the bedrock of all other measures.
Conclusion
Cybersecurity is not optional. Its importance becomes all too apparent when a successful attack takes place. But by then it may be too late to prevent significant damage. A cybersecurity framework that takes a holistic approach to these eight essential elements can give organisations the best chance of avoiding undesirable outcomes.
Sources
1 https://www.ft.com/content/728611e8-dce2-449d-bb65-cff11ac2a5bb
2 Sourced from explodingtopics.com as of December 2023 which quotes Statista as the source of information. Explodingtopics.com/blog/data-generated-per-day
3 IBM’s Cost of a Data Breach 2023 report
4 Sourced from explodingtopics.com as of November 2023 which quotes Thales Group as the sources of information. Explodingtopics.com/blog/corporate-cloud-data
5 CrowdStrike 2024 Global Threat Report.
6 Explodingtopics.com as of February 2024 which quotes Transforma Insights as the source of information. Explodingtopics.com/blog/number-of-iot-devices
7 National Health Executive, October 2018. GP refers to general practitioner.

